This article is based on a poster presented at the 2017 AIChE Spring Meeting and 13th Global Congress on Process Safety, San Antonio, TX, March 2017.
Here are some prevention and mitigation strategies for three common types of industrial incidents — a network breach, an insider attack, and infection via a portable device — and recommendations for incorporating industrial cybersecurity into an existing process safety management (PSM) program.
▲Figure 1. Manufacturing was the second-most-attacked sector in 2015. Source: Adapted from (1).
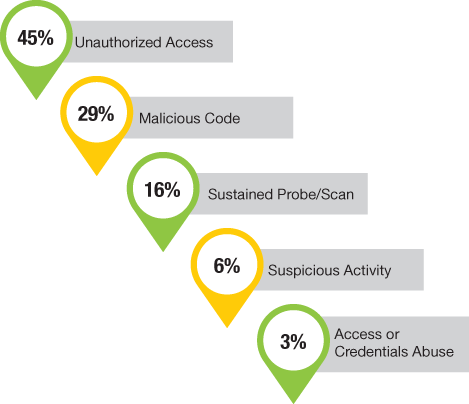
▲Figure 2. Unauthorized access accounted for almost half of the cybersecurity incidents reported in 2015. Source: Adapted from (1).
Cybersecurity has been in the headlines a lot recently, and breaches have affected everything from credit card data and personal health information to national elections. An analysis of cyberattack and incident data found that in 2015, manufacturing was the second-most-targeted industry (Figure 1); within manufacturing, chemical manufacturers were the second-most-targeted subcategory. Almost half of the security incidents involved unauthorized access (Figure 2) (1).
The U.S. Dept. of Homeland Security (DHS) regulates security at chemical facilities through the Chemical Facility Anti-Terrorism Standards (CFATS) and the Protecting and Securing Chemical Facilities from Terrorist Attacks Act of 2014 (2). DHS has so far identified more than 37,000 facilities with chemicals of interest (COI) that will be assessed further for security — including cybersecurity — vulnerabilities (3). Facilities ranked as high risk are required to evaluate, and if necessary improve, their security and will be subject to periodic inspection.
Process plants need to ensure that adequate safeguards are in place for a variety of upset conditions, including cybersecurity attacks that can result in loss of product, damage to equipment, downtime, and potential safety and environmental disasters (1). A cyberattack can infiltrate a process plant and wreak havoc on an industrial control system (ICS) — taking over the handling of hazardous chemicals, changing setpoints, disabling interlocks or cooling, etc., any of which could have serious, even catastrophic, consequences. Some attacks are designed to commit commercial fraud — for example, to compromise meters and cause them to register incorrect product transfers (i.e., more of less product, depending on which party is intended to benefit). Security breaches are also carried out for corporate sabotage to cause a competitor to lose money — by stealing intellectual property, causing unscheduled downtime and loss of product, or creating bad publicity and tarnishing a company’s public image (4).
This article examines three industrial incidents that employed common means of attack — a network breach, an insider attack, and a portable storage device. It discusses corresponding mitigation strategies and recommends next steps for incorporating industrial cybersecurity into an existing process safety management (PSM) program.
Would you like to access the complete CEP Article?
Buy CEP Article now for $9.95 Add To Cart
Are you an AIChE member or already own this?
Log In for instructions on accessing this content.
Copyright Permissions
Would you like to reuse content from CEP Magazine? It’s easy to request permission to reuse content. Simply click here to connect instantly to licensing services, where you can choose from a list of options regarding how you would like to reuse the desired content and complete the transaction.
